A highly-targeted, custom-built form of powerful Android malware is being deployed to conduct surveillance on selected individuals, according to security researchers.
Monokle is a sophisticated mobile surveillance ware that possesses remote access trojan functionality, advanced data exfiltration techniques as well as the ability to install an attacker-specified certificate to the trusted certificates on an infected device that would allow for man-in-the-middle (MITM) attacks.
These include keylogging, taking photos and videos, retrieving a history of apps including web browsers, social media services, and messengers, tracking the location of the user, and much more.
It has been spotted using novel techniques to exfiltrate data.
Monokle in the wild, the malware has the ability to self-sign trusted certificates to intercept encrypted SSL traffic. This allows the attackers to deploy unique capabilities in their quest to steal data.
While Monokle currently only targets Android devices, researchers say several samples of the malware contain unused commands and data transfer objects which point to the existence of an iOS version, suggesting the group would like to target iPhones in future.
The researchers said that the Special Technology Centre (STC) has been developing a set of Android security apps that share codes and command and control servers with Monokle.
The researchers noted that the samples they receive are built around trojanized versions of real and legitimate apps, complete with the same appearance and functionality.
Monokle RAT Work
Monokle doesn’t require root access on the device and makes extensive use of the Android accessibility services to access and grab data from third-party apps.
Even more impressively, it can record the device screen, steal the entered PIN or unlock pattern, and use predictive text dictionaries to figure out what topics the victim is mostly interested in.
Recording or even making calls, tracking the device location, getting the password salt, and retrieving calendar information is also possible for the malware.
Most of the owners of the infected devices never realize that they are getting monitored by Monokle. Some of the apps that have been found to contain the trojan include Skype, Evernote, Play Store, and U.C. Browser, so anyone could have fallen to the trap.

The icons used in different samples of Monokle. Most of these applications are trojanized versions of legitimate secure messaging, productivity, and popularly downloaded applications.
The icons and titles have also been stolen from these legitimate applications to disguise Monokle’s real purpose.
Other titles used familiar words like Google Update, Flashlight, and Security Update Service to appear innocuous to the intended target.
Prevention Tips
If you are worried about this possibly infecting your device there are things you can do to prevent this happening. You can at the least reduce the chance of getting it anyway.
Do not root your phone
Always check the app you are installing more than once. Check reviews and make sure you are actually on the Play store.
Do not install apps from third-party vendors.
We have talked about phishing prevention before.
Antivirus Android Application Defender Produced by STC
Defender is the antivirus Android application produced by STC. The About page that comes with this application mentions STC explicitly, lists the tool as a beta version (in the version being analyzed during this investigation), and also has the stc-spb.ru website included in the contact information.
Package name: defender.stc.com.defender
Links between Monokle and security software developed by STC
STC appears to offer a number of software products, but this report will focus on a suite of products that appears to be used as an Android defensive security solution, including a native antivirus engine, and a network monitor application, among others. This particular software allows us to link the work of STC with Monokle samples.
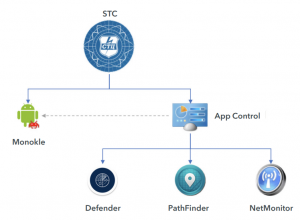
Command and control infrastructure that communicates with the Defender application also communicates with Monokle samples.
The signing certificates used for signing Android application packages overlap between Defender and Monokle as well.
Additional overlap was observed by Lookout researchers between Monokle and the defensive security software produced by STC in the authors’ development and implementation choices.
